Understanding Encryption: A Beginner’s Guide
Overview
Encryption is your digital shield. It turns your data into a secret code that only the right key can unlock. In a world full of hackers and prying eyes, understanding encryption is key to protecting your online privacy and keeping your personal information safe.
What is Encryption?
Imagine sending a letter in a locked box that only your friend can open. That’s encryption in a nutshell. It scrambles your data—whether it’s a message, a photo, or your banking details—so no one can read it without the key. I learned this the hard way years ago when an unsecured email account exposed my travel plans to a stranger. Encryption could’ve saved me that headache.
There are two types of keys: one-key systems (symmetric) and two-key systems (asymmetric). Symmetric uses the same key to lock and unlock, while asymmetric uses a public key to lock and a private key to unlock. Simple, yet powerful.

Why Encryption Matters
Every day, we share sensitive stuff online—passwords, credit card numbers, even our locations. Without encryption, anyone could grab that info. It’s like leaving your house unlocked in a busy city. Encryption ensures your data stays private, whether you’re shopping online or chatting with friends. It’s not just for tech wizards; it’s for everyone who values online privacy.
Types of Encryption
Let’s break it down: - Symmetric Encryption: One key does it all. Think of it as a single password. AES (Advanced Encryption Standard) is a popular example—it’s fast and used everywhere, like in secure messaging apps. - Asymmetric Encryption: Two keys, like a lockbox with a public drop slot and a private key to open it. RSA is a big name here, often used for secure website connections. Both have their strengths, and they often team up to keep us safe.
How Encryption Works
Here’s the magic: You type a message, and encryption software scrambles it using a key. The person on the other end uses their key to unscramble it. For example, when you see ‘HTTPS’ in a website’s address, asymmetric encryption sets up the connection, then symmetric takes over for speed. It’s seamless. I once watched a friend’s jaw drop when I explained how her bank app keeps her money safe this way—it’s everyday tech we take for granted.
Encryption in Action
Encryption isn’t just for spies. It’s in your life daily: - Online Banking: Keeps your transactions hidden. - Emails: Tools like ProtonMail encrypt your messages. - Messaging Apps: WhatsApp uses end-to-end encryption so only you and your friend see the chat. Next time you send a ‘happy birthday’ text, know it’s locked up tight.
Encryption and Online Privacy
With so much of our lives online, privacy is a big deal. Encryption stops snoopers from grabbing your data. Without it, your internet provider or a hacker on public Wi-Fi could see everything. I started using encrypted tools after realizing how much of my info was exposed on unsecured networks—peace of mind is worth it.

VPNs: Encryption’s Best Friend
VPNs, or Virtual Private Networks, are superheroes for online privacy. They encrypt your internet traffic, creating a secure tunnel from your device to the web. I use a VPN when traveling—hotels and airports are hacker hotspots. Your data gets locked up before it leaves, and only the VPN server unlocks it. No one else can peek.
Choosing the Right VPN
Not all VPNs are equal. Here’s what to look for: - Strong Encryption: AES-256 is top-notch. - No-Logs Policy: They shouldn’t track what you do. - Kill Switch: Cuts your internet if the VPN drops, keeping you safe. I’ve tested a few, and these features make a difference.
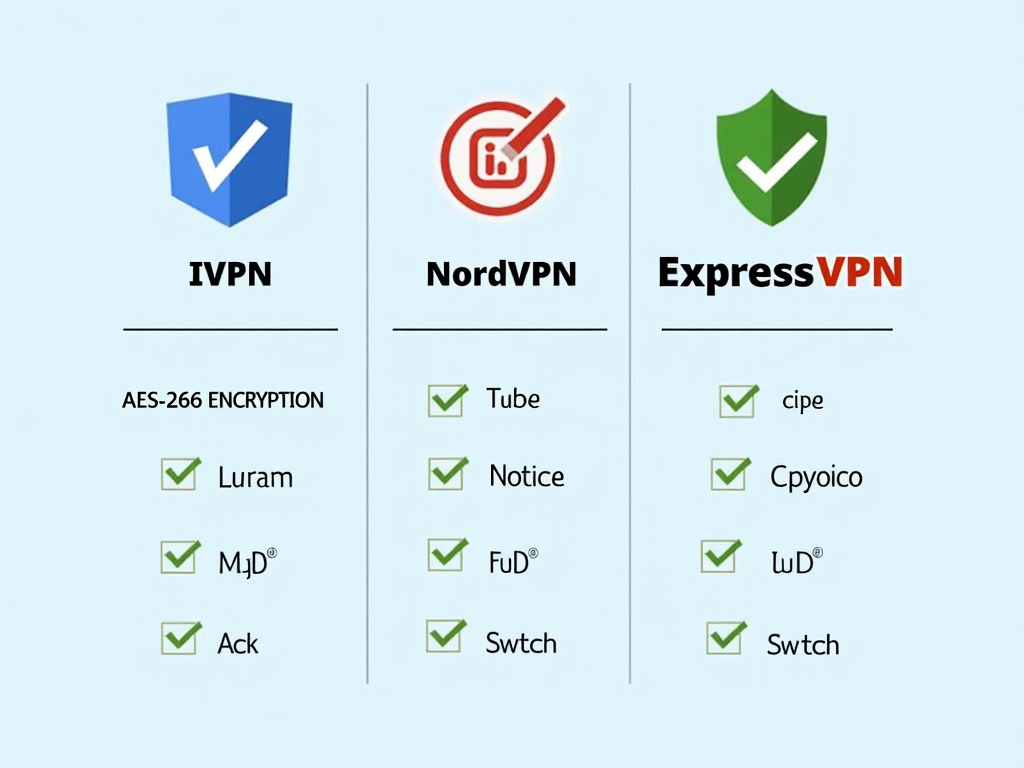
Here’s a quick look at some solid VPN options:
| VPN Provider | Encryption | No-Logs | Kill Switch |
|---|---|---|---|
| IVPN | AES-256 | Yes | Yes |
| NordVPN | AES-256 | Yes | Yes |
| ExpressVPN | AES-256 | Yes | Yes |
| These are reliable picks for keeping your data locked down. |
How to Configure IVPN on Android for Maximum Privacy
I’ve been using IVPN on my Android, and it’s straightforward: 1. Grab the app from the Google Play Store. 2. Log in with your account. 3. Pick a server—closer ones are faster. 4. Turn on the kill switch in settings. It took me five minutes, and now my phone’s data is secure, even on public Wi-Fi.

A Bit of Encryption History
Encryption isn’t new. Ancient Greeks used it to hide messages. Today, it’s evolved from simple codes to complex math protecting billions of devices. The Enigma machine in World War II was a game-changer—cracking it helped win the war. Now, that same idea keeps your Netflix binge safe.
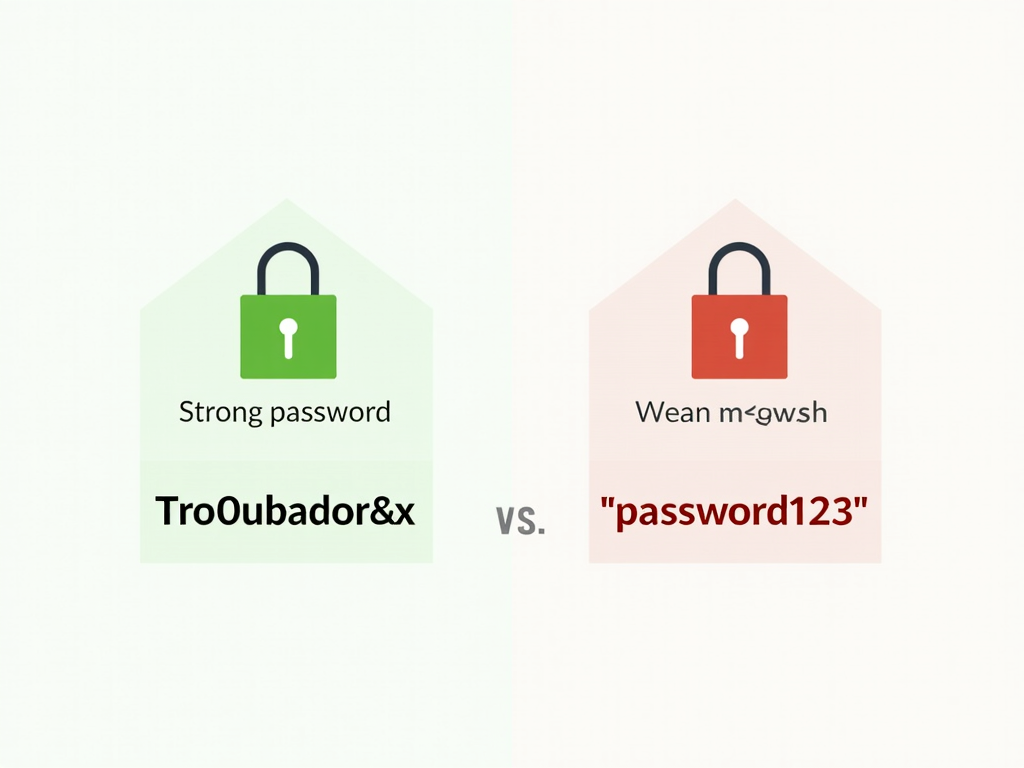
Passwords and Encryption
Strong passwords boost encryption. A weak one is like a flimsy lock—easy to pick. Use at least 12 characters, mix in numbers and symbols, and don’t reuse them. I started using a password manager after forgetting too many, and it’s a lifesaver paired with encryption tools.
Summary
Encryption is your key to a safer online life. It protects your data from prying eyes and powers tools like VPNs to boost your online privacy. From banking to texting, it’s everywhere, and understanding it puts you in control. Start small—try a VPN or secure messaging—and feel the difference.