Understanding End-to-End Encryption: A Beginner’s Guide
In today’s digital world, privacy is more important than ever. With so much of our personal and professional lives happening online, protecting our data from prying eyes is crucial. One of the most effective ways to do this is through end-to-end encryption. But what exactly is it, and why should you care? In this guide, we’ll break down the concept of end-to-end encryption in simple terms, explain how it works, and show you why it’s a must-have for anyone who values their online privacy.

What Is End-to-End Encryption?
At its core, end-to-end encryption (E2EE) is a method of secure communication where only the sender and the receiver can read the messages. No one else—not even the service provider, hackers, or government agencies—can access the content of your messages. This is because the data is encrypted on your device before it’s sent and can only be decrypted by the intended recipient’s device.
Think of it like sending a letter in a locked box. Only the person with the key (the recipient) can open the box and read the letter. Even if someone intercepts the box along the way, they won’t be able to see what’s inside without the key.
Why Is End-to-End Encryption Important?
End-to-end encryption is essential for protecting your privacy and ensuring that your sensitive information remains confidential. Here are a few reasons why it matters:
- Privacy Protection: Whether you’re sending a personal message, sharing financial details, or discussing confidential business matters, E2EE ensures that only the intended recipient can access the information.
- Security Against Hackers: Even if a hacker manages to intercept your data, they won’t be able to read it because it’s encrypted.
- Trust in Services: Many popular apps and services, like WhatsApp, Signal, and even some email providers, use E2EE to build trust with their users by prioritizing privacy.
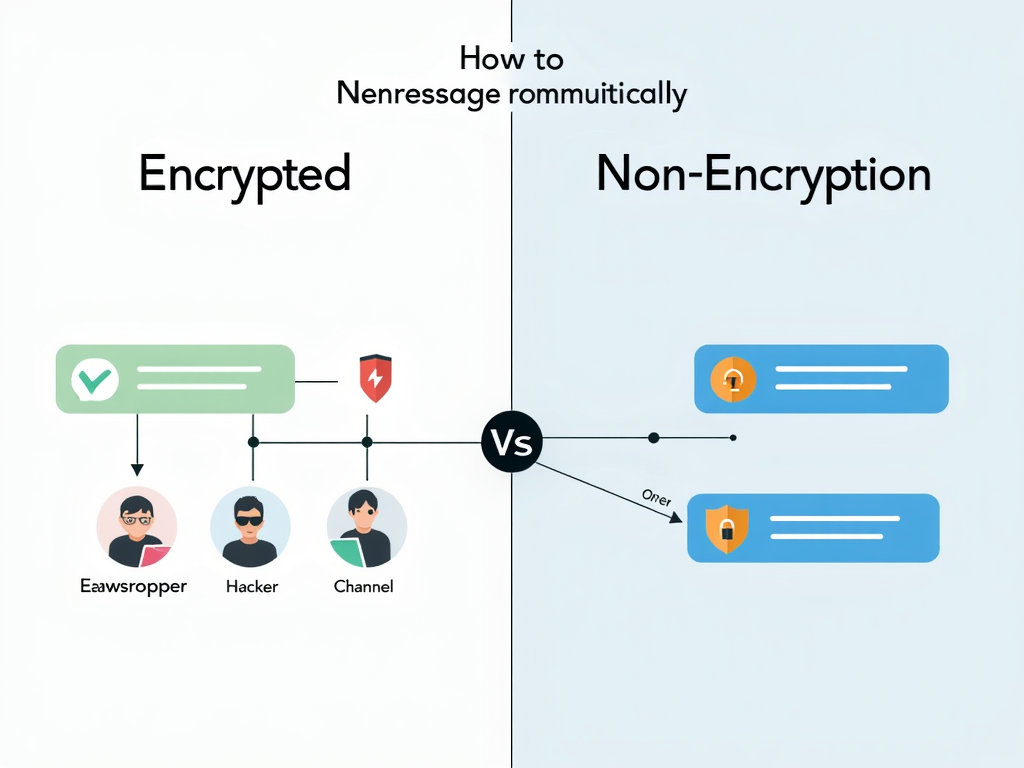
How Does End-to-End Encryption Work?
End-to-end encryption uses complex mathematical algorithms to scramble your data into an unreadable format. Here’s a simplified breakdown of how it works:
- Key Generation: When you send a message, your device generates a unique pair of keys—a public key and a private key. The public key is shared with the recipient, while the private key stays on your device.
- Encryption: Your message is encrypted using the recipient’s public key. This turns the message into a jumbled code that can only be unlocked with the recipient’s private key.
- Transmission: The encrypted message is sent over the internet. Even if it’s intercepted, it’s useless without the private key.
- Decryption: The recipient’s device uses their private key to decrypt the message, turning it back into readable text.
This process happens automatically in the background, so you don’t need to be a tech expert to use it. Many apps and services handle the encryption for you, making it accessible to everyone.
Common Misconceptions About End-to-End Encryption
Despite its importance, there are some common misconceptions about end-to-end encryption that can confuse beginners. Let’s clear up a few:
-
Myth 1: It’s Only for Tech-Savvy People
Reality: Many popular apps, like WhatsApp and Signal, use E2EE by default. You don’t need to be a tech expert to benefit from it. -
Myth 2: It’s Too Complicated
Reality: E2EE works seamlessly in the background. You can send encrypted messages just as easily as regular ones. -
Myth 3: It’s Not Necessary for Everyday Use
Reality: Whether you’re chatting with friends or handling sensitive work documents, E2EE protects your data from potential threats.

Real-World Applications of End-to-End Encryption
End-to-end encryption isn’t just for messaging apps. It’s used in a variety of services to protect your data:
- Messaging Apps: WhatsApp, Signal, and Telegram (in secret chats) use E2EE to secure your conversations.
- Email Services: Providers like ProtonMail offer end-to-end encrypted email, ensuring that only you and the recipient can read your messages.
- Cloud Storage: Some cloud storage services, like Sync, Internxt, and pCloud, use E2EE to protect your files. This is especially important when storing sensitive documents online. For a detailed comparison, check out our article on the Best cloud storage for privacy: Sync vs Internxt vs pCloud.
- Video Calls: Apps like Zoom and FaceTime use E2EE to secure your video and audio communications.
Choosing the Right Tools for Online Privacy
When it comes to protecting your data, not all services are created equal. Here’s a quick look at some popular tools that prioritize end-to-end encryption:
| Service | Type | E2EE Enabled | Key Features |
|---|---|---|---|
| Messaging | Yes | Automatic encryption, large user base | |
| Signal | Messaging | Yes | Open-source, highly secure |
| ProtonMail | Yes | Encrypted email, no access to user data | |
| Sync | Cloud Storage | Yes | Zero-knowledge encryption, file sharing |
| Internxt | Cloud Storage | Yes | Decentralized storage, privacy-focused |
| pCloud | Cloud Storage | Optional | Encrypted folders, file versioning |
When choosing a service, consider your specific needs. For example, if you’re looking for secure cloud storage, you might want to compare options like Sync, Internxt, and pCloud to see which one offers the best balance of security and usability.
The Future of End-to-End Encryption
As online privacy becomes a growing concern, the demand for end-to-end encryption is only going to increase. Governments and tech companies are constantly debating the balance between privacy and security, but one thing is clear: E2EE is here to stay.
In the future, we can expect more services to adopt this technology, making it the standard for secure communication. Whether you’re a casual user or a privacy enthusiast, understanding how E2EE works and why it’s important will help you make informed decisions about the tools you use.
Summary
End-to-end encryption is a powerful tool for protecting your online privacy. By ensuring that only you and the intended recipient can access your data, it provides a level of security that’s essential in today’s digital age. From messaging apps to cloud storage, E2EE is used in a variety of services to keep your information safe. As you navigate the online world, look for tools that prioritize encryption and make privacy a core part of their offering.